If your organization has been successful since before containers were a thing, then you probably already have a mix of static on premise machines and short-lived DevOps infrastructure. Introducing a separate secrets management or credential provider creates islands of security that will make it difficult to control and gain visibility into your organization’s access and security posture. With the integration between Conjur Enterprise and CyberArk Enterprise Password Vault (EPV) you can now obtain an enterprise-wide source of truth for secrets management across all environments.
When to use Conjur Enterprise vs Other CyberArk Products
Companies need a tool that suits the dynamic nature of DevOps environments without compromising the level of security that the CyberArk Privileged Access Security (PAS) product suite provides. For many non-dynamic environments, our customers use CyberArk Application Identity Manager (AIM) to securely retrieve secrets from the CyberArk Vault. AIM is secure and works well for the aforementioned use case, but it isn’t as suited for the dynamic world of DevOps. Conjur was designed to works with elastic or dynamic environments. The integration between EPV and Conjur Enterprise allows customers to sync their existing secrets into their DevOps environment and secure access from short-lived hosts to existing privileged resources.
Introducing the CyberArk Vault Synchronizer
CyberArk offers the Vault-Conjur Synchronizer to ensure that that secrets are available across the enterprise. With the Synchronizer, secrets stored and managed in the CyberArk Vault are automatically and safely pushed to Conjur and used by its clients, APIs, and SDKs. The integration between Vault and Conjur enhances security in DevOps environments, including CI/CD pipelines, containerized applications, and cloud platforms. This forms a consistent, unified, and enterprise-wide privileged access security solution.
How the Synchronizer Uses Line of Business to Provide Role Based Access
One important element of the Synchronizer is the existence of a ‘line of business’ (LOB). An LOB is a method of organization that defines groups according to their required secret access. This separation increases security by barring other teams within the organization from accessing secrets that are not used within their defined area of work. The Synchronizer creates LOBs in Conjur according to those that the Vault admin configured. After the synchronization establishes the LOBs in Conjur, the Conjur LOB admin (i.e the team leader) performs the delegation of secrets to the appropriate users and hosts.
Example
The following example depicts how the Synchronizer allows clients to manage a secret in the vault and then use it in one of Conjur’s DevOps integrations – Conjur’s Ansible module.
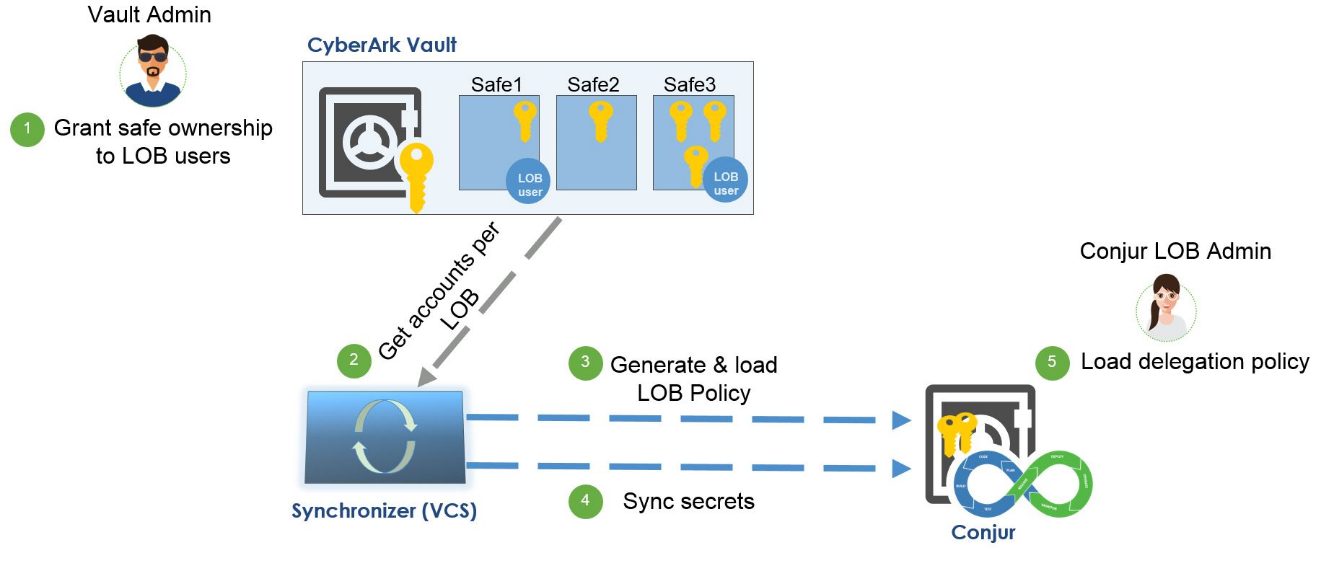
Meet Jeff, our Vault admin, and Lisa, our Conjur LOB admin. Lisa is using Conjur’s Ansible module to inject a secret into an Ansible task, while the secret is managed in the Vault. Jeff stored that secret in the Vault and configured the rotation policy of that secret — with Central Policy Manager (CPM) — to every 7 days. To sync the secret with Conjur, Jeff creates an LOB in the Vault and includes that secret in the LOB. Jeff’s work is done, and the Synchronizer steps in.
The Synchronizer periodically refreshes to retrieve LOBs from the CyberArk Vault. For each LOB, the Synchronizer identifies any new or updated accounts in the Vault and creates or updates secrets hosted in Conjur accordingly. In under 5 minutes, Lisa can use the secret stored by Jeff in her Ansible playbook.
Conclusion
The CyberArk Vault Synchronizer allows customers to work with the latest, advanced DevOps tools while reaping the benefits of CyberArk’s PAS suite and Conjur. For both dynamic and non-dynamic environments, the Synchronizer creates a uniform solution to secrets management by centrally managing access (secrets) and enforcing consistent security policies.
Oren Ben-Meir is a Software Engineer at CyberArk. He is passionate about exploring new areas, both in code bases and around the world. Oren loves to pass on the knowledge and experience he acquired along the way and guide others in their own personal journey.
