After much hard work, our team is pleased to announce the release of our new v3 of CyberArk/Conjur Puppet module with support for Puppet v6 and additional enhancements! This Conjur Puppet module release significantly modernizes the project while simplifying the Puppet user experience. The new Conjur v3 Puppet module release can be downloaded from either Puppet Forge or GitHub.
What’s New?
Key enhancements:
- Increased security
- Reduced complexity
- Support for Puppet compilation primary servers
- Improved documentation
- More automated testing
There are many exciting improvements to talk about, but we will focus on highlights:
Support for Puppet v6. With Puppet 5 approaching end-of-life and our users starting to move to Puppet v6, we have converted all of our code to Puppet v6-compatible code. By enabling our code to run on this version of Puppet, we’re helping to ensure that our users can run the plugin on the latest Puppet infrastructure. As part of this modernization, we have also created a dedicated v2 branch of our plugin so that users of deprecated features can still use our module until they can make the full conversion to our Puppet 6-compatible v3 release.
Use of Deferred functions. With support for Puppet 6 enabled, we have updated the module to use Deferred functions, which enables our module to retrieve CyberArk Dynamic Access Provider (DAP) / Conjur variables directly from the agent. By interacting with Conjur strictly on the agent in all use cases, users can increase deployment security by reducing the credential attack surface. Using variables retrieved via Deferred functions uses slightly different templates, but the overall usage is similar. However, this change means that the v3 module is incompatible with the Puppet v5 which does not support Deferred functions. If you are still using Puppet v5 you can continue to use the v2 module branch.
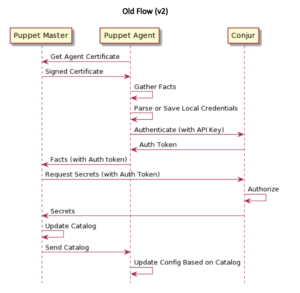
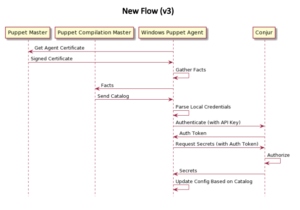
Support for multiple compilation servers. In this release, the module works more seamlessly on all scales of deployment, including Large and Extra-Large configurations by leveraging Deferred functions. This is a significant improvement over the v2 module, which only works with Standard Installation Puppet Architecture as there is no compilation server support.
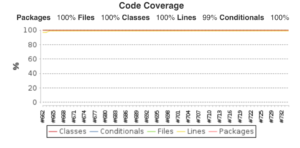
Improved architecture. Version 3 also brings many improvements to the internal working of the module with a streamlined code base, more test coverage (100% conditional test coverage and 99% line test coverage), improved stability and automation. In addition, new support for Puppet Development Kit automates many of our manual processes. With our improved automated testing of compilation server and Windows platform, this release represents a massive jump in simplicity, automation and verifiable quality.
V3 Code Coverage Results
Puppet API Tutorial
The use is really simple if the agent is pre-configured:
$dbpass = Deferred(conjur::secret, ['prod/psql/password'])
If you want to provide inlined or Hiera-provided parameters, you can do so as well. Note that authn_api_key must be wrapped as a Sensitive value to prevent it from being accidentally logged by Puppet:
$sslcert = @("EOT")
-----BEGIN CERTIFICATE-----
…
-----END CERTIFICATE-----|
-EOT
$dbpass = Deferred(conjur::secret, ['prod/psql/password', {
appliance_url => "https://my.conjur.org",
account => "myaccount",
authn_login => "host/myhost",
authn_api_key => Sensitive("your_api_key"),
ssl_certificate => $sslcert}])
})
To use the value retrieved, you either pass it directly to a method that natively supports Sensitive values (most of the built-ins do) or you can manually use it (e.g. in a template). If you choose the latter option, you must use Deferred methods for the templating as templates are by default evaluated before Deferred functions. The following example shows both usages:
node 'server-123' {
$db_password = Deferred(conjur::secret, ['prod/db-password'])
# Example of writing a secret to a file
file { '/tmp/creds.txt':
ensure => file,
mode => '0600',
content => $db_password,
}
# Example of using a secret in a templated file
file { '/tmp/creds.ini':
ensure => file,
mode => '0600',
content => Deferred('inline_epp', [
'password=<%= $db_password.unwrap %>',
{ 'db_password' => $db_password }
]),
}
}
For additional details on the module check out our Puppet Forge page.
Future Plans
We welcome, and are closely watching for, further user feedback so we can continuously improve our module and make using secrets from DAP and Conjur a breeze!
Feel free to reach out to us on GitHub and let us know if you have any issues or suggestions!
Resources
Version 3 of CyberArk/Conjur module is Certified by CyberArk and can be installed from:
Talk to Us
If you enjoy this Puppet module or have questions, please let us know in the CyberArk Commons Community forum. We are always looking for feedback and input on new features and integrations.
Until Next Time
Stay tuned,
CyberArk Community and Integrations Team
Srdjan Grubor is a Software Engineer at CyberArk where he is building the next-generation digital security products. Srdjan is the author of “Deployment with Docker” book, was one of the first people to receive a Docker Certified Associate certification, and has worked on Linux systems at scale for over a decade. He enjoys breaking things just to see how they work, tinkering, and solving challenging problems.