Learning is fun, and the best way to learn is through hands-on exercises. That’s why Conjur provides some tutorials to help you learn about security automation.
When following along with online tutorials, it can be a hassle to install all the software, plugins, and libraries you need to get everything working on your computer. To simplify your learning experience, Conjur’s Katacoda-based interactive tutorials enable you to walk through actual procedures and see the results without installing anything or even creating an account. All you need is a web browser!
Simply head over to Secrets Management Hosted Tutorials to get started. In this article, we provide an overview of each tutorial, and what to expect from your hands-on learning experience.
Secure Ansible SSH Keys and Secrets in Ansible Playbooks
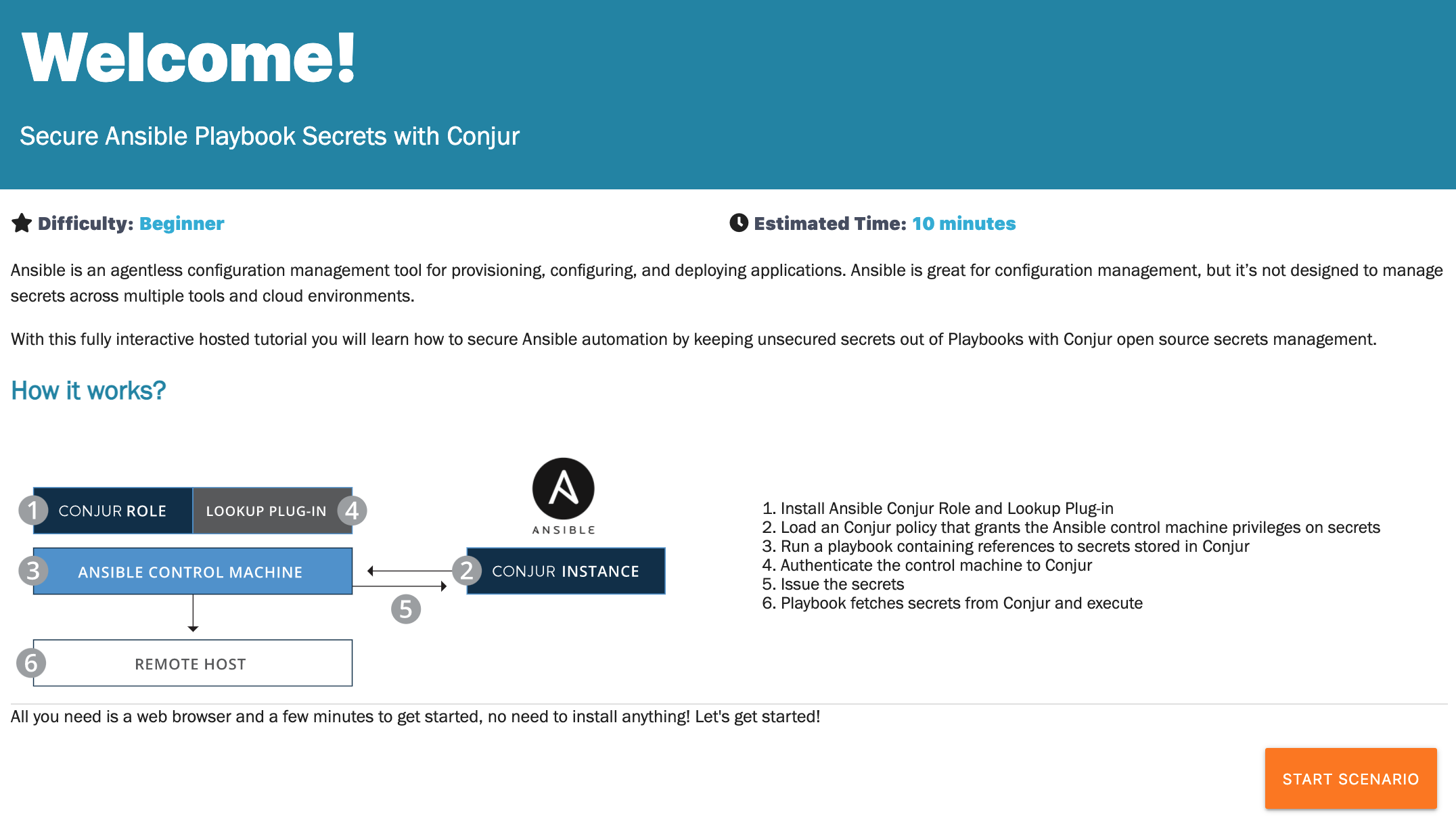
The first interactive tutorial teaches you how to use Conjur open source secrets management to secure secrets in your Ansible Playbooks. Ansible is an agentless configuration management tool for provisioning, configuring, and deploying applications. It’s great, but it’s not designed as a secrets management solution that manages secrets across different tools and cloud environments.
With Conjur’s security automation, you can securely manage your secrets. This interactive 10-15-minute tutorial shows you how.
Every tutorial starts with an overview of the scenario and how it works:
 In all tutorials, you’ll have access to a server, which is accessible from a console in your browser. You can then follow the steps and executable commands on the left side of the screen.
In all tutorials, you’ll have access to a server, which is accessible from a console in your browser. You can then follow the steps and executable commands on the left side of the screen.
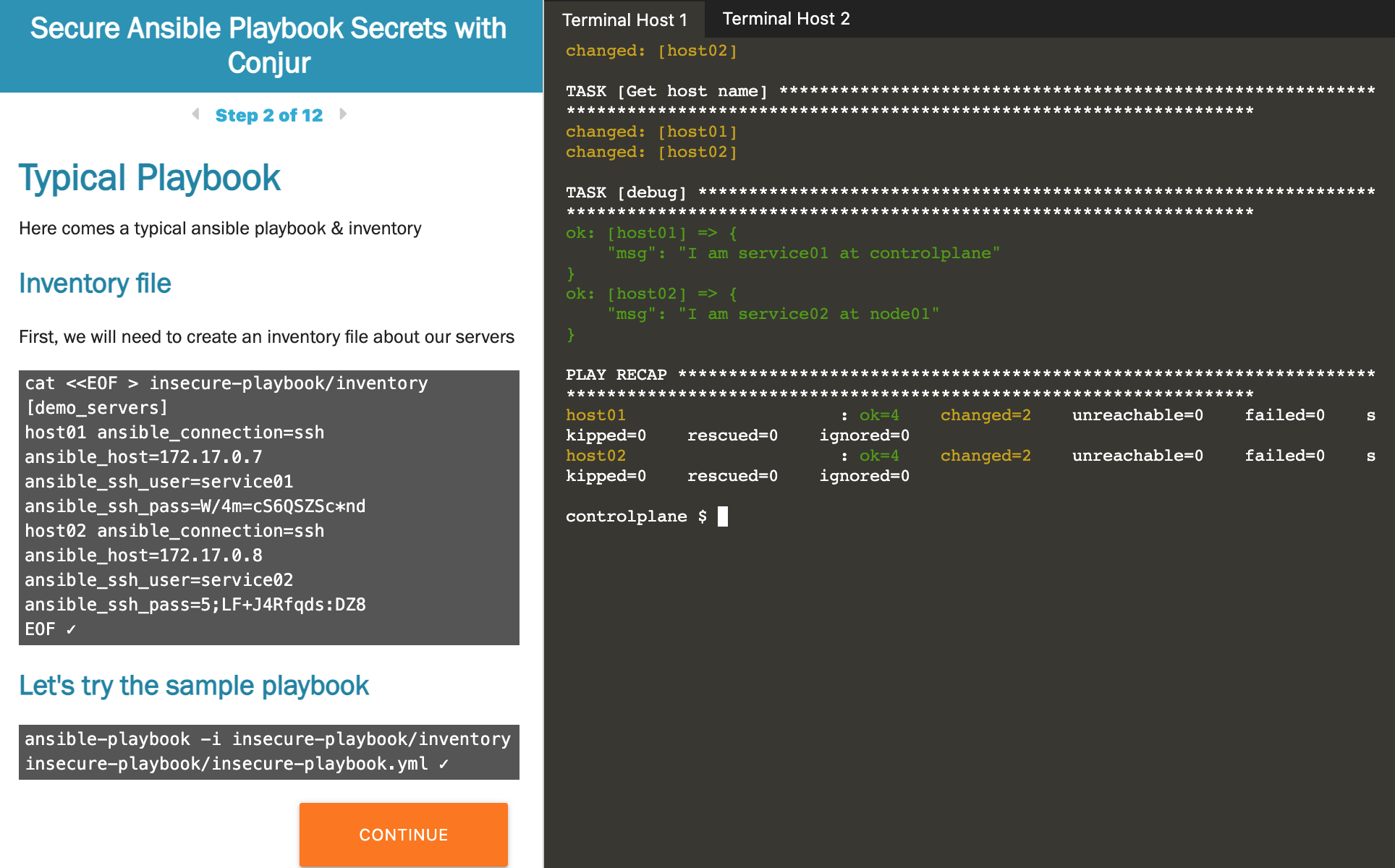
In this tutorial, you’ll first see why Ansible is insufficient for secrets management. Next, you’ll create an (anonymous and disposable) Ansible account using the embedded console and use it to secure your Ansible Playbook. At the end of this tutorial, you’ll have secured your Ansible secrets using Conjur.
Secure CI/CD Pipelines by Removing and Securing Secrets Within Jenkins
Protecting continuous integration and continuous deployment (CI/CD) pipelines is even more important after the SolarWinds breach. This incident reveals how advanced attackers are compromising developer environments to inject malicious code into software supply chains.
Jenkins is one of the most popular CI/CD build systems for DevOps pipelines. It and other CI/CD tools are designed to build and deliver applications, but they also have access to many sensitive secrets across the entire DevOps environment. This is especially risky when secrets are exposed in Jenkinsfiles and other configuration files that are checked into code repositories like GitHub.
In addition to protecting against attackers, it’s also important to acknowledge which employees, customers, and suppliers may have access to this CI/CD environment. Company or client secrets are exposed to all these people if you do not secure the secrets sufficiently.
In this interactive tutorial, you’ll get a complete Jenkins environment and detailed explanation on how to incorporate Conjur with Jenkins for improved CI/CD security.
Like the Ansible tutorial, this tutorial includes steps with access to a server through a console.
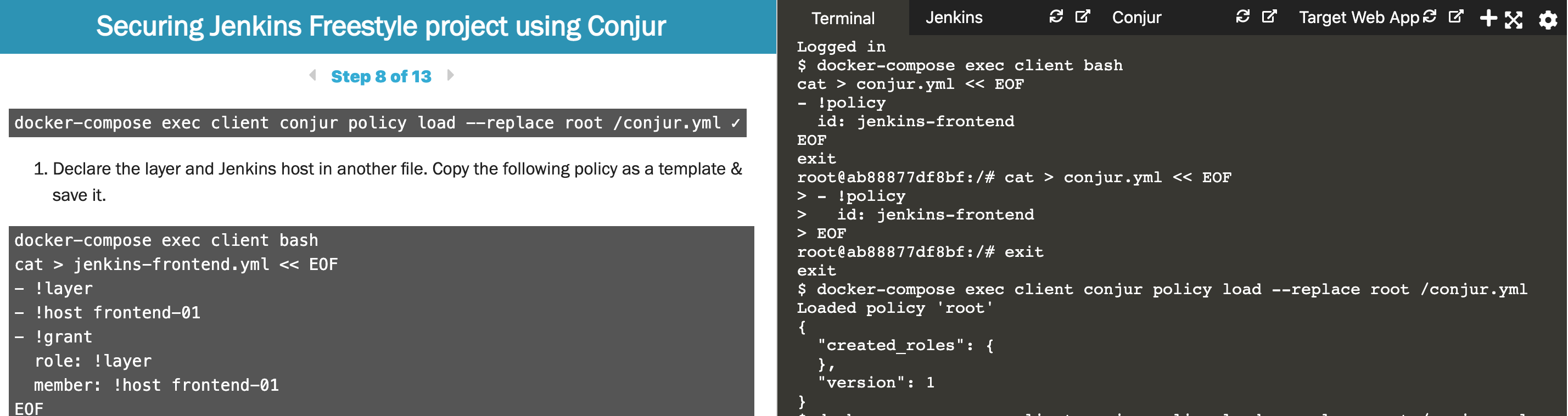
With Conjur, you can manage your secrets in a single location. Updating your secret in Conjur updates it for Jenkins, Ansible, GitHub, and wherever you use that secret. These CI/CD tools access the credentials they need while Conjur still keeps your secret a secret.
Secure Kubernetes Secrets with RBAC, Native Authentication, and Secretless Broker
Kubernetes is one of the most popular container orchestration platforms. Its open-source framework automates deployment and management of container-based applications. Kubernetes is relatively new and quickly evolving, there are still widely-recognized best practices for securely managing secrets.
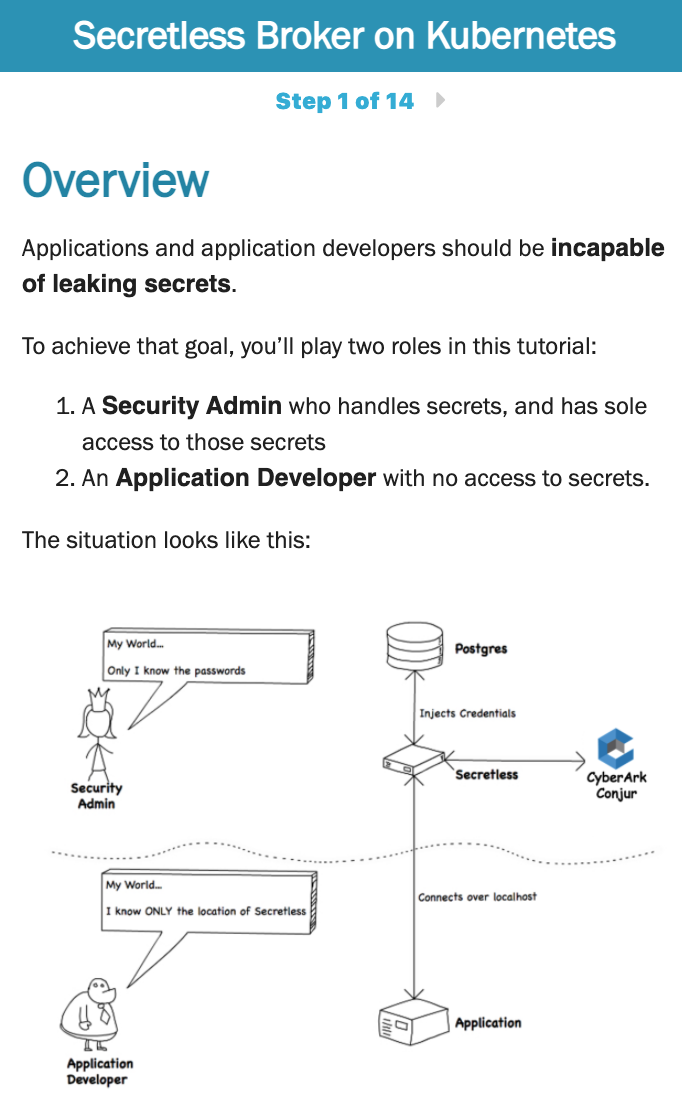
This Kubernetes secrets tutorial starts with describing why a developer should not know secrets, only their location.
The Kubernetes security tutorial is, again, a mix of an interactive command window and steps to follow, with an occasional image for clarity.
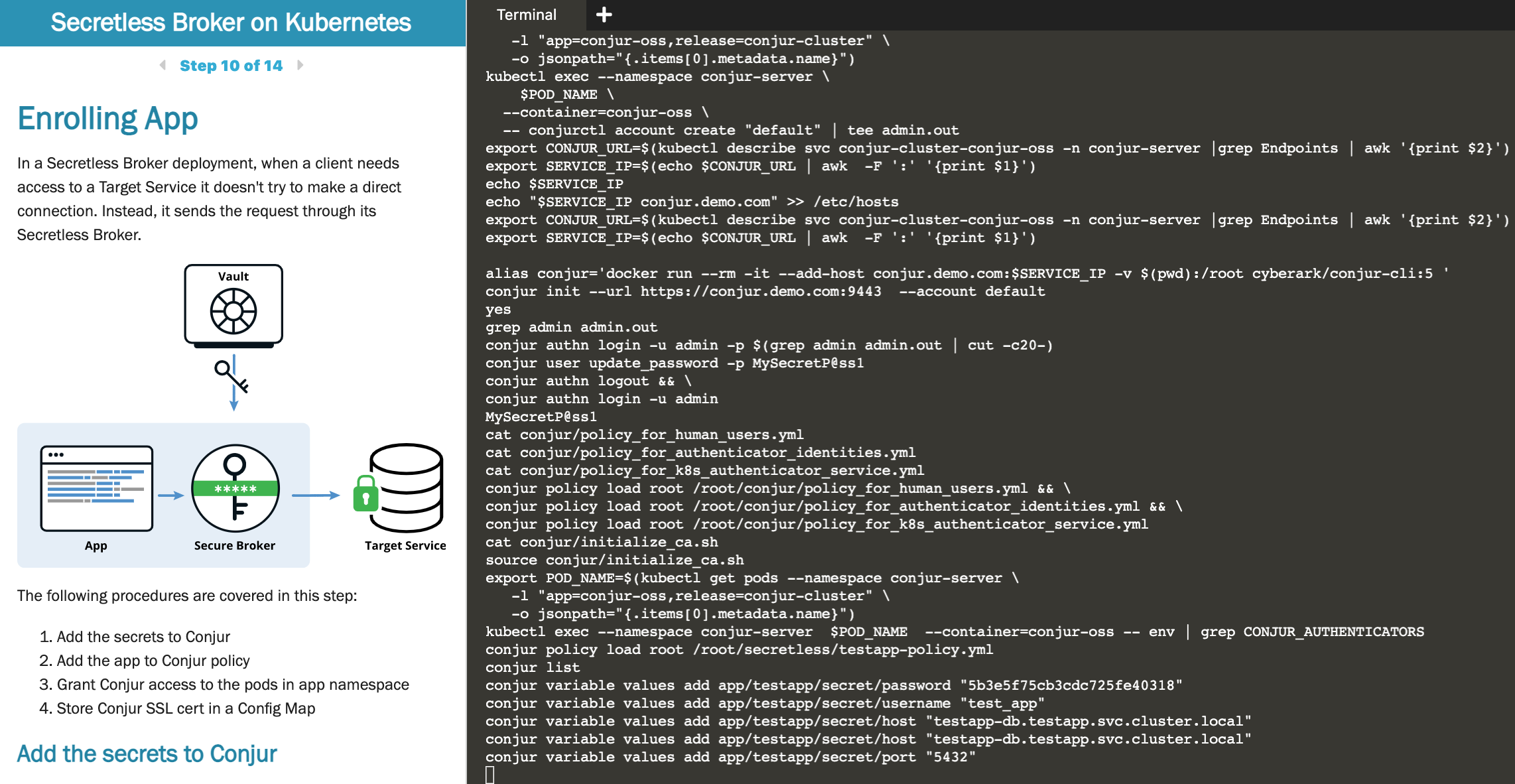
You’ll actually take on two roles in this tutorial, that of the secret administrator and that of a developer. With role-based access control (RBAC), each role will only have access to what they need.
At the start of the Kubernetes security tutorial, you’ll have a dockerfile with a database username and password in clear text. At the end of the tutorial, these values will be set to dummy values and the actual values will come from Conjur. This helps prevent secrets leaks in a Kubernetes environment.
Conclusion
Getting started with Conjur’s interactive secrets management tutorials is easy and just two clicks away! The first click takes you to the interactive tutorials list and the second selects the tutorial you want. The tutorials are aimed at beginners and take around 10 to 15 minutes each, so you can complete one on your lunch break and be Conjur-savvy in no time.
You’re welcome to join our developer community, reach out to us (or fellow developers in our forum), sign up for the monthly DevOps newsletter to get the latest news, or check out our other security automation blogs to learn more about how CyberArk Conjur helps improve your cloud security.

John Walsh has served the realm as a lord security developer, product manager and open source community manager for more than 15 years, working on cybersecurity products such as Conjur, LDAP, Firewall, JAVA Cyptography, SSH, and PrivX. He has a wife, two kids, and a small patch of land in the greater Boston area, which makes him ineligible to take the black and join the Knight’s Watch, but he’s still an experienced cybersecurity professional and developer.