Introduction
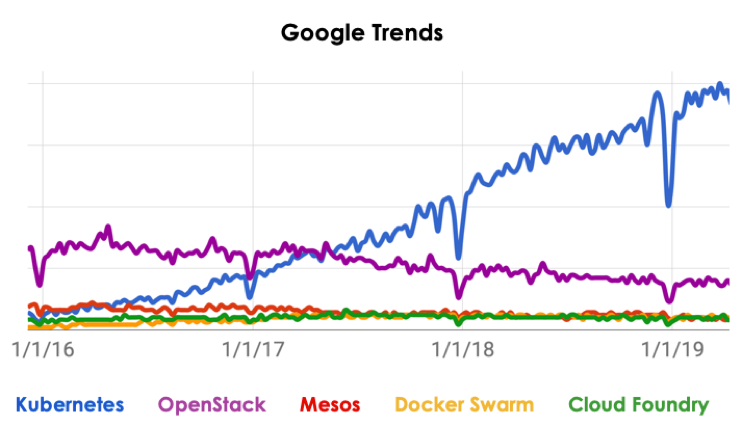
KubeCon is the premiere conference for the Kubernetes and cloud-native communities. Every year it is held jointly with CloudNativeCon, hosted by the CloudNative Computing Foundation (CNCF), which is the governing body for cloud-native open source projects and its largest and, arguably, most important project is Kubernetes. Both KubeCon and Kubernetes have received increasing attention over the last few years. KubeCon attendance has grown at a rate of 50% to 100% year-over-year and google search volumefor Kubernetes is trending steadily upward. This growth underscores the importance of what happens at KubeCon and with Kubernetes.
Kubernetes Google Search Trends
KubeCon +CloudNative Con Attendance 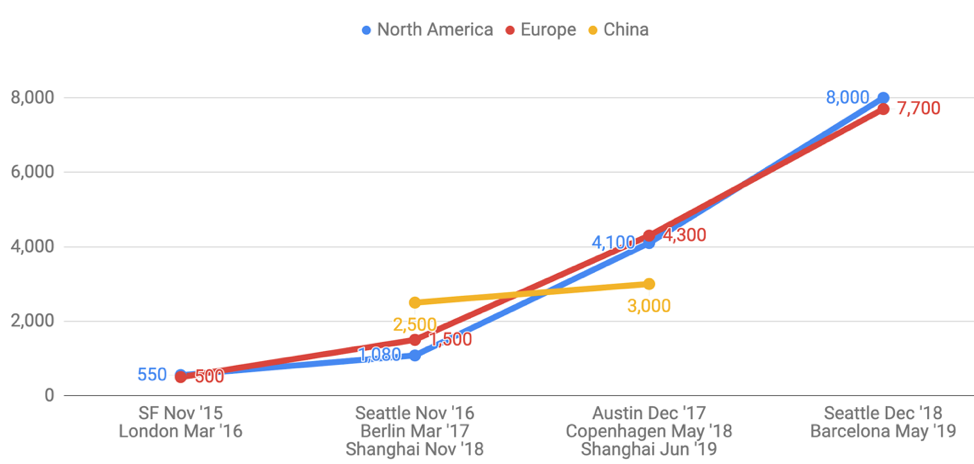
Why Barcelona was the right place for KubeCon Europe 2019
This year KubeCon was held in beautiful Barcelona, Spain (though my former engineering manager and Catalonian friend Bruno assures me Barcelona isn’t really part of Spain). There are many things to love about Barcelona, but its most famous landmark is the Sagrada Familia. Interestingly, this basilica is best known for still being unfinished after 137 years. This massive project has benefited from contributions from some of the worlds most talented architects and artist. The results speak for themselves. This as this building is truly stunning, even in its unfinished state. Regardless of your religious affiliation, no one can dispute the architectural innovation and artistry that the Sagrada Familia exhibits. In many ways, the Kubernetes community project represents a similar achievement, since it brings together many technical visionaries and architects to build something that will evolve and improve over time. Like the Sagrada Familia, Kubernetes isn’t finished and, with every KubeCon conference, we get to see how it’s grown. This is the reason that Barcelona was the perfect place to hold KubeCon + CloudNativeCon Europe 2019.
This Year DevOps Security Experts Voices are Heard at KubeCon
I was fortunate enough to attend KubeCon in Seattle last year and KubeCon Barcelona this year. You can read my Seattle KubeCon wrap-up here. It’s interesting to see how this conference and Kubernetes itself have evolved and continue to evolve over just 5 short years. It’s a slightly more rapid pace than the Sagrada Familia, give or take 130 years. The biggest changes from last year were the addition of the “Security + Identity + Policy” track and the creation of the CNCF Security SIG. There were security talks at KubeCon last year and there are numerous Kubernetes related security projects, but this new track shows that security has a more prominent voice in the Kubernetes community and that the security architects are helping to shape Kubernetes.
What changed?
One of the most severe Kubernetes vulnerabilities ever, CVE-2018-1002105, was discovered late in 2018. Ian Coldwater, Lead Planform Security Engineer from Heroku, gave a fascinating analysis of the nasty Kubernetes bug from the point of view of a security enthusiast. For those of you who didn’t hear the talk, this CVE has a base score of 9.8 out of 10 and is considered critical. If the vulnerability isn’t patched, an attacker can establish a connection through the Kubernetes API server and then use the same connection to directly access backend servers without having to authenticate again. Ian explained that this happened because security teams hadn’t completely caught up with Kubernetes and the rest of cloud-native universe yet. To me, this mirrors the DevOps security story— innovation and operational speed came first without much regard for security until massive breaches like the one that happened to Uber brought security to the forefront.
Kubernetes and CNCF Security take a Step Forward
Tthe CNCF Security SIG was introducedat KubeCon. There is a long and complicated history regarding how the CNCF community is governed in terms of SIGs and WGs. To simplify things, let’s say that the WGs were a less formal and sometimes unofficial part of the CNCF governing body. CyberArk’s Geri Jennings has been a part of the SIGs journey from SAFE WG to CNCF Security SIG. The Security SIG gives security professionals a more formal and prominent seat at the CNCF table, which governs Kubernetes.
KubeCon Roundup
There was so much going on at KubeCon that it was impossible to do and see everything that I wanted. Twistlock had an interesting demonstration on how to host a Capture the Flag (CTF) with Kubernetes. Datadog had standing room only for its talk: “10 Ways to Shoot Yourself in the Foot with Kubernetes, #9 Will Surprise You.” Our Security SIG friends presented a deep dive into the plan for the groups and how the community can help. There was also some interesting discussion about SPIFFE, a platform-agnostic identity layer that can be used to authenticate and secure workload communication.
What this means for Kubernetes
Today, June 7, Kubernetes celebrates its fifth birthday and with age comes maturity. The addition of security talks at KubeCon and the formalization of the CNCF Security SIG demonstrate Kubernetes’s maturation in terms of security. No great open source project will ever truly be done. Open source projects like Kuberenetes are collaborations full of competing voices and visions that bring together a special blend of expertise and the time to iteratively improve. Much like Antoni Gaudi’s Sagrada Familia, our work is still ongoing. I just hope that we are all here to see that vision 130 years from now.
Next Steps
We have made some exciting improvements to Conjur.org and we would love to get your thoughts. Please join our monthly newsletter to keep informed about the latest DevOps and open source news. Join the CyberArk Commons to talk with us directly, ask question or give us your feedback. Check out our new Conjur getting started tutorials.

John Walsh has served the realm as a lord security developer, product manager and open source community manager for more than 15 years, working on cybersecurity products such as Conjur, LDAP, Firewall, JAVA Cyptography, SSH, and PrivX. He has a wife, two kids, and a small patch of land in the greater Boston area, which makes him ineligible to take the black and join the Knight’s Watch, but he’s still an experienced cybersecurity professional and developer.
