No matter their occupation, nobody likes to do the same set of tasks repetitively — especially when automation is an option. At some point, things get boring. Plus, there are inefficiencies, productivity bottlenecks, and manual execution errors. This is particularly true when performing such tasks on a larger scale.
Most people would rather spend their time doing work that challenges their intellect, and automate repetitive and boring tasks. The need for automating everyday tasks in the IT industry birthed an open-source automation tool called Ansible.
Let’s learn more about Ansible and explore how secrets management works in Ansible Tower, and discuss how it integrates with Conjur to better manage your secrets.
Ansible and its “Tower”
Ansible Helps Automate Tasks
Ansible is an open-source automation tool that IT professionals use to perform tasks like application deployment, configuration management, security and compliance audits, continuous delivery, intraservice orchestration, and provisioning.
System engineers and IT administrators must regularly perform a list of actions across many servers in a particular sequence of steps. The conventional way to do this is to execute hundreds of commands, but this approach is rather daunting and error-prone. Some “smart guys” develop scripts to run the commands. But as much as it makes the work easier, it requires coding skills, and time to develop and maintain these scripts, too. Not many people are able to pick up these skills, so they settle for the option of drudgery.
This is where Ansible comes in. Ansible changes the approach from long scripts to short and simplified playbooks that are easy to develop and maintain. Tasks that previously required hundreds of lines of script code take only a few lines of instruction in an Ansible playbook.
Also, an inventory can group servers and apply instructions to them simultaneously. Interestingly, this whole process requires little to no coding skills, taking IT professionals a step forward in their ability to automate.
Ansible Tower Makes Ansible User-Friendly
As much as Ansible’s technology helped alleviate the problem of tedious and repetitive tasks, it isn’t exactly user-friendly. And that’s putting it mildly. Ansible’s complexity makes it especially challenging for new users to get comfortable with the application before drilling down to learn how to create playbooks and inventories. Users yearned for an intuitive interface to manage quick deployments and monitor configurations.
Ansible Tower (and its open-source version AWX) is a web-based interface explicitly created for managing Ansible. It solves Ansible’s user-friendliness problem, tremendously increasing ease of use for all kinds of IT teams.
Ansible Tower’s Features
Ansible Tower makes Ansible more suitable for large enterprises, acting as a hub for all automation tasks and providing a dashboard that summarizes all hosts’ states. Ansible Tower also increases deployment speed and helps monitor all configurations.
Ansible Tower allows sharing Secure Shell (SSH) credentials without exposing them, which is not possible with plain Ansible. It logs all jobs, manages inventories graphically, and synchronizes them with a wide variety of cloud providers. With Ansible, you can only run playbooks from the command line, but Ansible Tower gives you a nice graphical view to choose the playbooks you want to run.
In addition to the visual dashboard, Ansible Tower supports role-based access control (RBAC), which maintains security and streamlines user access management. In other words, it gives different users varying access privileges. For example, user one can only access playbooks one and two, and user two can only access playbooks three and four.
Ansible Tower can also schedule jobs. When you need to run a job at a specific time or at particular intervals, you can simply schedule Ansible Tower to run these jobs. As well, real-time job updates provide insight into job and automation status. These updates let the user know which jobs ran successfully and which failed.
Ansible Tower also has an integrated notification feature to notify specific team members when a job runs successfully or fails. In addition, Ansible Tower supports multi-playbook workflows and has REST APIs that integrate well with Jenkins and Red Hat Satellite servers. It also uses PostgreSQL for database management.
Ansible Tower’s Secret Management System
Secrets Management Challenges
Ranging from passwords for our computers to door locks for our homes, we all use some form of an access management system. We do this to prevent unauthorized access to our property or essential information. We don’t want to carelessly leave our passwords where any random person can access them.
Similarly, access credentials and secrets are an essential component in infrastructure management. It’s imperative to keep them safe from compromise. Otherwise, the entire environment is at risk.
One challenge common to many systems administrators when managing infrastructure and deploying automation with Ansible is the challenge of managing secrets and sensitive data. Exposing credentials and secrets may pose a severe threat.
In most cases, someone doesn’t expose these secrets intentionally. They may inadvertently share secrets in public code repositories like GitHub. Or, over-privileging in DevOps tools with access may reveal the secrets.
Managing Secrets in Ansible
Ansible is a powerful tool, but it isn’t tailored for managing secrets across various applications and cloud environments. For instance, you may have a configuration file or playbook that requires a password or some other piece of critical and sensitive information. While you know that storing such information directly in your playbook isn’t a great idea, you are also not exactly sure where to keep it.
Ansible management introduced a secret management system into Ansible Tower to resolve this challenge. As a user or administrator, you can upload cloud credentials to Ansible Tower, enabling access to machines and external services on your behalf.
When you need to use the secrets that you have stored in the external system, you can simply fetch them ahead of the job execution to run a playbook. Ansible Tower manages three sets of secrets, including user passwords for local Ansible users, Ansible Tower operational secrets such as database password and message bus password, and secrets for automation such as SSH keys, cloud credentials, and secret tokens for external services.
Welcome to Security Island
Ansible’s Tower’s secret management is great, but it’s not enough on its own. Enterprises running modern hybrid and multi-cloud environments won’t be able to manage their entire infrastructure with Ansible. This can cause security islands, where, for example, an enterprise has its application secrets spread among multiple platform-specific secrets managers like Kubernetes Secret, Azure Key Vault, and AWS Secrets Manager. Security islands make it challenging to implement centralized audit and access control or delegate authority to manage subsystems using well-defined standards.
As a result, the security landscape becomes complicated and increasingly difficult to manage when companies scale up. Security teams choose their own unofficial tools and policies to ease their work. This approach isn’t proper, but they can’t help it. This is mainly because they must find a way to deliver.
Fortunately, Conjur offers a solution. It integrates with nearly every platform’s secrets management tool and lets you keep all of your company’s secrets in a single, secure location.
By separating secret management from application code, Conjur takes the burden of dealing with application security away from developers so that they can focus on their primary task of developing application functionality. It also integrates easily with existing infrastructure, enabling secure identification, control, and auditing across various environments.
CyberArk Conjur manages secrets using strong, multifactor authentication without requiring that any additional modules be installed. Ordinarily, most secret protection methods usually have one master secret that protects all other secrets — known as secret zero. The drawback of this is that compromising the master secret compromises the entire system. Cyberark Conjur takes away the problem of secret zero, using multi-factor authentication which ensures that a combination of attributes (only available to trusted containers) are used to authenticate login, instead of just one attribute making it impossible for the entire system to be compromised when one credential is stolen. These attributes may include IP Address, UUID, and Cryptographic keys.
How Ansible Tower Integrates with Conjur
To integrate Conjur with Ansible Tower’s secret management system, you first create an external credential. Then, you select CyberArk Conjur Secret Lookup as the credential type. You also fill in other necessary details in the New Credential dialog, as the image below indicates:
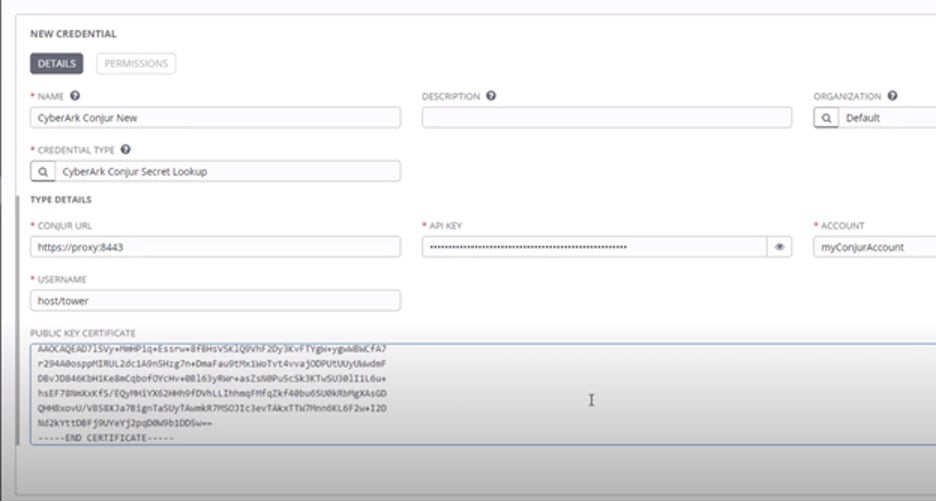
By doing this, you avoid manually entering secrets like passwords when carrying out your configurations. You simply refer to the password variable, and Conjur fetches it. This approach helps keep your secrets secret and makes it possible for your security teams to carry out their work seamlessly.
You can get a more detailed explanation of the steps to follow in the video Deploying And Using CyberArk Conjur With Ansible Tower. Or, read our walkthrough to learn how to deploy Conjur using Ansible Tower .
Summary
Repetitive tasks feel like drudgery, especially on a larger scale, and risk human errors. Ansible technology helps solve this problem by automating IT tasks like application deployment, configuration management, security and compliance audits, continuous delivery, and more. However, Ansible is not built for managing secrets, hence the need for Ansible Tower.
Ansible Tower’s secret management system integrates well with CyberArk Conjur, ensuring Secure Ansible Automation without stranding Ansible on a security island. To experience secrets management in Ansible for yourself, test out the CyberArk Conjur security features, and give your security teams and clients a much more seamless experience, dive in and start using Conjur and Ansible Tower together.
Check out the following articles for more information about secrets management:
- Simplifying secrets management with CyberArk and Red Hat Ansible Automation Platform
- Security Islands: What are they, and how can you avoid them?
- Secrets Management Hosted Tutorials
- Secrets Management Overview For Developers & DevOps

John Walsh has served the realm as a lord security developer, product manager and open source community manager for more than 15 years, working on cybersecurity products such as Conjur, LDAP, Firewall, JAVA Cyptography, SSH, and PrivX. He has a wife, two kids, and a small patch of land in the greater Boston area, which makes him ineligible to take the black and join the Knight’s Watch, but he’s still an experienced cybersecurity professional and developer.
