Kubernetes is a popular choice for microservices because it provides scalable, portable, efficient deployment and reduces most DevOps overhead. Generally, in Kubernetes, we configure many types of secret keys such as HTTP access keys, SSH access keys, cryptography keys, and many more. When these keys are stored in Kubernetes, they are vulnerable to attackers who breach the network.
In 2020, a survey found that nearly 80% of companies experienced one or more cloud data breaches in the past 18 months. Due to vulnerabilities, it’s too often possible for attackers to breach data and mishandle information. For example, there was a data breach in Tesla’s cloud storage in 2018. Hackers entered Tesla’s Kubernetes, which did not require authentication. From there, they used the stored SSH keys to access an Amazon Web Services (AWS) account and mine cryptocurrency. In addition to wasted company resources, mishandled secrets mean mishandled user privacy, as attackers find and steal company, employee, and customer information.
The burden of secrets management can be as frustrating for developers as it is concerning for security teams. No one wants to take the blame for mismanaged secrets. However, there are several ways developers and DevOps engineers can secure their applications.
For one, developers should never use hardcoded credentials.
At the same time, DevOps engineers should use best practices to maintain application security, including providing role-based access control (RBAC), granting required permissions only, and rotating credentials, among many other precautions.
However, the added benefits of these security solutions come with the disadvantages of increased overhead and hard operability for DevOps teams.
To easily secure Kubernetes applications, we can use an open-source secrets management tool like Conjur. It seamlessly integrates with most cloud providers and DevOps tools to provide a centralized view of security. Best of all, you don’t need to be a security expert to use it.
In this tutorial, we’ll learn more about Conjur and explore four methods to create secure apps for Kubernetes.
Conjur Architecture
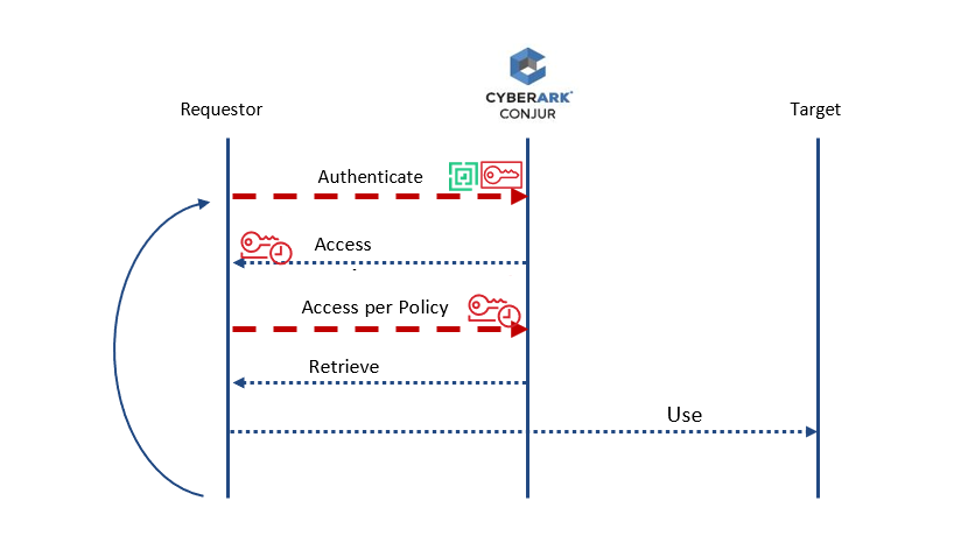
Conjur acts as middleware to provide centralized application security. The architecture can be divided into three main sections — requestor, Conjur, and target. The requestor requests an access token from Conjur, then, according to the granted access policy, is redirected to the target.
How to Secure a Kubernetes Application
There are many ways to secure Kubernetes applications. To do so without manually managing secrets, you can use REST API, summon, Kubernetes Secrets, or Secretless Broker.
You can view a detailed video tutorial on the Cloud Native Computing Foundation website.
Using REST API
You must perform three steps to secure Kubernetes using REST API:
- Set up an authenticator instance running as a sidecar (a helper container for various purposes within the cluster).
- Run an application that uses a REST API to pull credentials from a database.
- Connect to the database using these credentials.
The GET request to Conjur to retrieve secrets looks like this:
GET /secrets/{account}/{kind}/{identifier}{?version}
You can also use curl:
curl -H “$(conjur authn authenticate -H)” \
https://eval.conjur.org/secrets/myorg/variable/prod/db/password
CyberArk provides API libraries to help you integrate Conjur into your development environment.
Using Summon
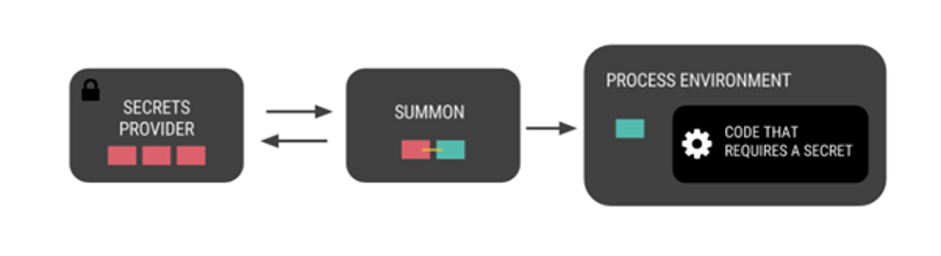
The diagram below explains the summon injection workflow. Basically, with summon, we retrieve secrets from the authenticator init container and transfer them to the environment requiring the secret.
This method has two steps:
- Set up an authenticator instance to run as an init container.
- Use summon to pull credentials and call the application with credentials in environment variables.
We enter the init container using the command:
kubectl exec -ti <container_name> /bin/bash
Then, we use the following command to get the secrets, which will then inject into the container environment:
summon env
This command will look into the secrets.yml file of the init container and then retrieve the secrets. The downside of this method is that if the application wants to retrieve the secret again, or if the secrets are changed, the container needs to restart.
When the application has the secrets, we can connect to the database.
Head over to GitHub to learn more about summon.
Using Kubernetes Secrets
Kubernetes also provides built-in secrets management and uses summon to retrieve secrets for use in the application.
This method has three steps:
-
- As you would in the summon method, set up an authenticator instance to run as an init container.
- Create Kubernetes secrets with conjur-map as an identifier in the string data. For example:
conjur-map: String - Username: [username_path in secret provider] - Password: [password_path in secret provider]
- Now, create a Kubernetes secret for use in the application.
- The authenticator retrieves DB credentials and dynamically patches a K8s secret with DB credentials. Retrieve secrets by executing into the init container and running the inject command. Or, you can run ./exec_into_app.sh inject in your environment, which will do the same thing. This will retrieve secrets present in conjur-map and store them in K8s secrets.
Using Kubernetes Secrets, you can connect to the application.
Using Secretless Broker
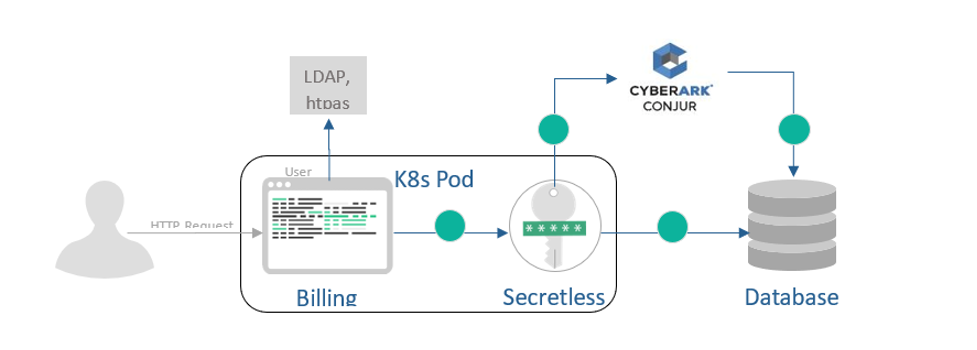
This diagram shows how Secretless Broker works. All connections go through this broker and it authenticates and authorizes the secrets from a remote database.
This method has three steps:
- Run an authenticator as a sidecar container listening on a database port. This means every authentication request will go through this authenticator. We are also running our application as an initial container connected to the local port database.
- Check the proof of retrieval. When an application connects to a database on a local port, the authenticator will proxy the connection and retrieve the database credentials from the remote database.
- An app will use these credentials to connect to the database.
You can also check out Conjur’s interactive demo.
Benefits of Conjur
Conjur provides a simple, context-free, and secure method for retrieving credentials in containers. The transferred data within is encrypted end-to-end using SPIFFE-compliant resource identifiers. Most importantly, the credentials are not exposed to any third party or middleware, as they reside only in memory.
Conjur provides a consistent, programmatic interface that simplifies application development by offering a centralized platform for secrets management and controlling access to non-human identities. Developers can more easily secure, audit, store, and fetch secrets across continuous integration and continuous deployment (CI/CD) tool stacks, containers, and cloud platforms, spending less time learning secrets management tools and more time delivering value.
Next Steps
In this article, we learned about Kubernetes secrets and how we can build secure Kubernetes applications faster with the help of the open-source secrets management tool Conjur. We covered four different secrets management methods for your application.
With this knowledge, you can secure your own containers and systems to reduce the chance of data breach, then explore Conjur’s other helpful container management tools.
Check out Conjur’s Secretless Broker on Kubernetes tutorial to get started and join our large, and growing, open source community of developers just like you.

John Walsh has served the realm as a lord security developer, product manager and open source community manager for more than 15 years, working on cybersecurity products such as Conjur, LDAP, Firewall, JAVA Cyptography, SSH, and PrivX. He has a wife, two kids, and a small patch of land in the greater Boston area, which makes him ineligible to take the black and join the Knight’s Watch, but he’s still an experienced cybersecurity professional and developer.