The Application Developer Access Dilemma
As application developers, we need secure access to resources – such as databases, SSH servers, and HTTPS based resources – for our enterprise applications. Secrets are the means by which our applications can access these protected resources. To do our job and obtain secure access, we need to write application code with API calls or use environment variables to fetch secrets from a secure vault, like Conjur. Then we make the call to the protected resource, i.e. a database, SSH server or HTTPS web service.
This approach is secure when we follow best security practices, but it puts some of the responsibility for secrets management and security on application developers and makes our job (writing code) more difficult. Developers don’t want to handle secrets, but we need to be sure that our applications can access secure resources and services outside of the application.
How Developers can get Access Without the Hassle of Handling Secrets
As developers we just want access, but do we really want to handle or manage the secrets that grant this access? I’d much rather be delivering business value and writing code. The Conjur Secretless Broker feature isolates applications and developers from secrets while brokering the access they need. Secrets belong in a vault like Conjur, not in code, scripts or applications and Secretless Broker helps make this possible.
What is Secretless Broker?
Secretless Broker is an independent and extensible open source community project maintained by CyberArk. Today Secretless Broker works within Kubernetes and OpenShift container platforms with Conjur, Application Access Manager’s Dynamic Access Provider and Kubernetes Secrets vaults.
The Secretless Broker enables applications to connect securely to services and other resources without ever having to fetch or manage secrets. Conjur Open Source offers the Secretless Broker capability to application developers as a way to isolate their applications from secrets. This reduces the developer’s burden of securely handling and fetching secrets from a vault, thus streamlining secure application development and making applications more secure.
Secretless Broker Simplifies How Applications Securely Access Resources
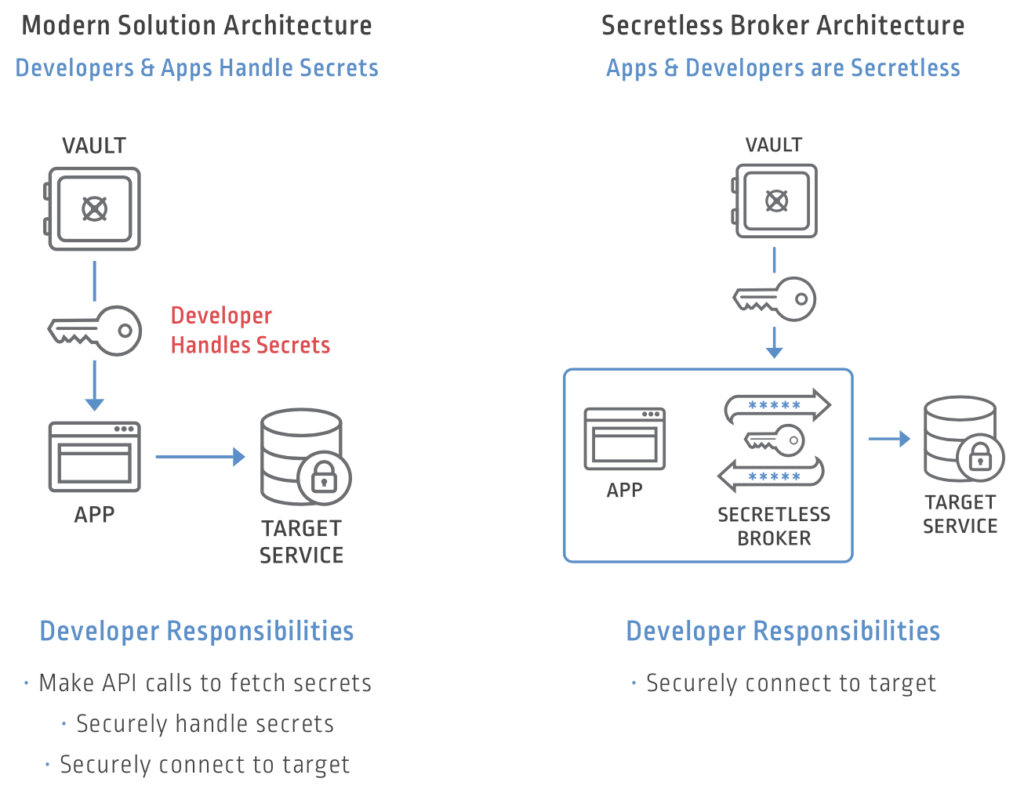
How Does Secretless Broker Work?
When an application needs to securely access a resource, instead of using secrets directly, the application simply makes a local connection request to Secretless Broker, which then automatically authenticates the application, fetches the required secret from a vault like Conjur and establishes a connection to the database.
From the developer’s perspective:Instead of needing to include code in our application to fetch the secrets from the vault and then use the secret to access the protected resource, the developer simply configures the application to connect to the required resource via the Secretless Broker.
From the security team’s perspective: Secrets can no longer be inadvertently logged or exposed by the application. With Secretless Broker, the application code does not get access to the credential, so it cannot leak secrets. Applications can’t leak what they don’t have!
Next Steps
To get started with a Secretless Broker or to learn more about it, take a look at the Secretless Broker page on Conjur.org here. If you are new to Conjur, check out our Conjur quick start tutorial. Don’t forget to join our monthly newsletter to keep informed about the latest DevOps and open source news. Join the CyberArk Commons to talk with us directly, ask question or give us your feedback on the Secretless Broker, Conjur, Summon, and other CyberArk open source projects.
Be sure to register for the Secretless Broker webinar: “Security Win: Giving Developers the Access They Need Without the Hassle via Secretless Broker”, at 1pm EST, 5 September.

John Walsh has served the realm as a lord security developer, product manager and open source community manager for more than 15 years, working on cybersecurity products such as Conjur, LDAP, Firewall, JAVA Cyptography, SSH, and PrivX. He has a wife, two kids, and a small patch of land in the greater Boston area, which makes him ineligible to take the black and join the Knight’s Watch, but he’s still an experienced cybersecurity professional and developer.